Table of Contents
How to obtain a personal certificate
Overview
A certificate is basically a key that can be used to sign or encrypt documents and that has some further information attached to it, like who it belongs to or how long it will be valid and so on. What makes it a certificate is the fact that some authority certifies that this key is authentic and belongs to you. This is the public part of a key-pair used in a public-key infrastructure. In order to get a working certificate you need to do the following:
- generate a key-pair
- the public key, which becomes the certificate
- the secret key, which you always must keep for yourself
- have some certification authority approve your certificate
- publish your certificate to
- allow other users to verify signatures that you created using your secret key
- allow other users to decrypt documents that you encrypted using your secret key
- allow other users to encrypt documents that only you can decrypt using your secret key
For the first step, creating the key-pair, we will use the Firefox web browser. The certification authority in the second step will be the FU-CA, the certification authority of Freie Universität Berlin, in this case represented by the registration authority (RA) at the physics department, which means at some point in the process you'll have to walk to the office of Jens Dreger and have him check your personal ID (Personalausweis).
This process will create a personal certificate which is valid even outside of the FU. The reason why this works is that the FU-CA will sign your certificate with their own certificate, which in turn is signed by the DFN-Verein (Deutsches Forschungsnetz) certificate which again has been signed by Deutsche Telekom Root CA. So once an application (e.g. a web browser) trusts the certificate from Deutsche Telekom, it will trust the authenticity of your personal certificate.
Creation of a key-pair and certificate request
We will do this in the Mozilla Firefox browser since it is available on all operating systems and it's easy to find the created key-pair later on, since it stays in the browser. Please note that for the whole process you need to use the exact same computer and browser. So don't start this at work and try to finish it at home.
Start Firefox and visit the DFN-PKI page for physics users. Click Nutzerzertifikat and fill in the necessary information:
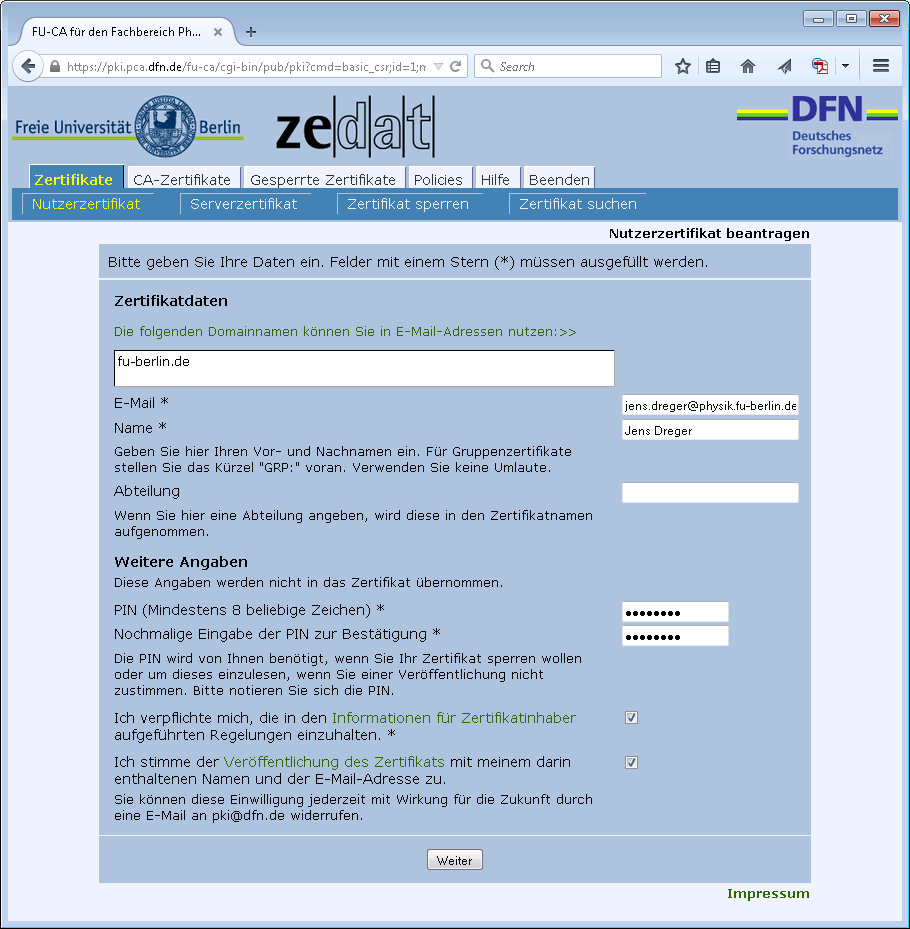
While the first checkbox is mandatory, the second is optional. If you select the second checkbox your certificate will be published by the DFN website, e.g. it will be found using the Zertifikat suchen function. If you want to enable other users to send you encrypted email, you probably should enable publishing your certificate. After two more clicks you should print out and sign your certificate form, which looks like this:

Approval of your certificate request
Take this printout to Jens Dreger and bring an ID (Personalausweis). After your certificate has been approved you will receive an email:
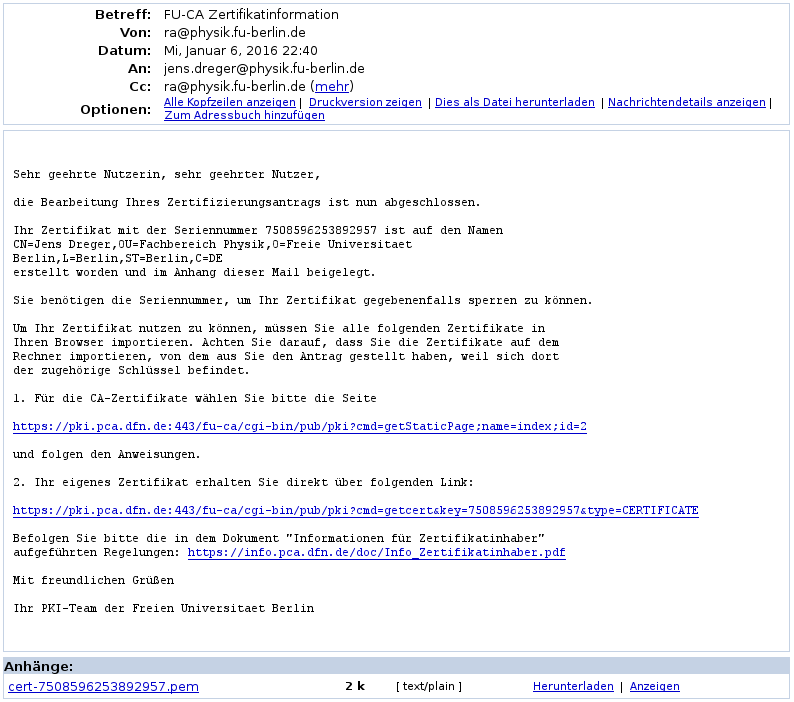
The attachment to this mail is your certificate file. This is the public part of your key-pair and the secret key is still stored inside your browser. You now need to join these keys and export both. To do so click the second link in the email message and you should be taken to a page that looks like so:
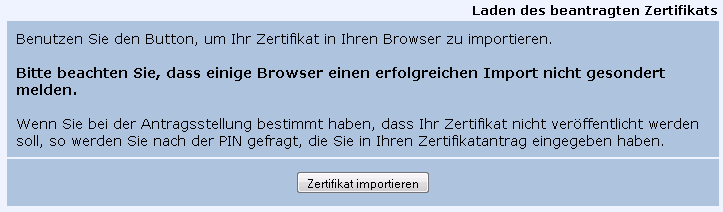
Click on Zertifikat importieren and you should receive a message like:
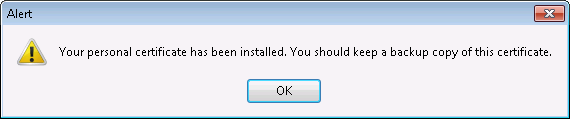
If you get some error message like This personal certificate can't be installed because you do not own the corresponding private key which was created when the certificate was requested you have most likely mixed computers or browsers.
Export your certificate and secret key to a file
You have now joined the signed certificate containing your public key and the secret key inside the browser certificate store. Go to Options → Advanced → View Certificates and select the Your Certificates tab. You should find your certificate:
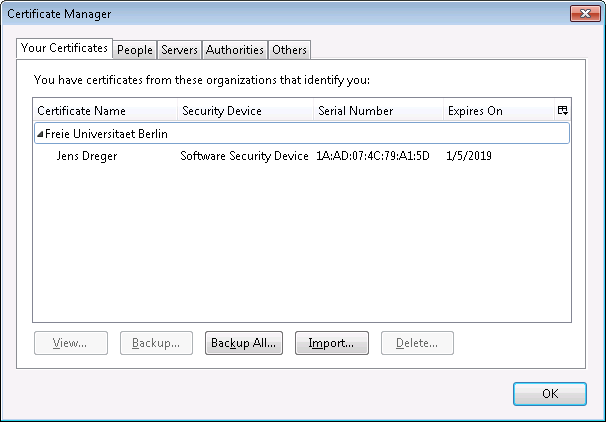
Select your certificate, choose Backup… and save the certificate to a PKCS12 file (default). You will be asked for a password. This password is used to encrypt the secret key inside the PKCS12 file so than no one can use your secret key unless he knows this password. Later when signing a document using your key you will be asked for this password:
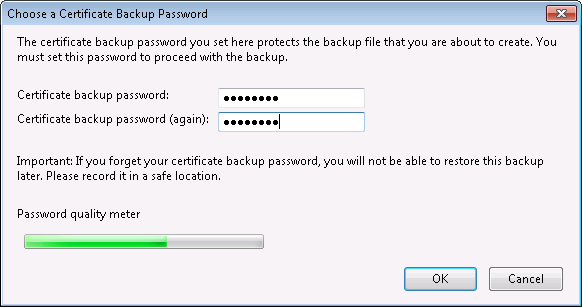
It makes sense to give that file a name that refers to the certificate inside, for example use the serial number as stated in the email message (7508596253892957 in this case). The .p12 file itself is encrypted and can not be read easily.
Next we'll see how to use your personal certificate to sign PDF documents.
